Adding Groups when using SAML JIT in Workspace ONE Access
In this Blog we unravel the intricacies of integrating groups seamlessly into the SAML Just-In-Time (JIT) provisioning process within Workspace ONE Access. Navigating through this often mystifying terrain, we address a key challenge – adding groups – a task not directly facilitated through the GUI of Workspace ONE Access . Instead, we’ll guide you through the realm of APIs, unlocking the potential for enhanced functionality.
We acknowledge the comprehensive resource available at Omnissa TechZone, offering a foundation for basic API usage with Workspace ONE Access. To avoid redundancy, we encourage you to refer to this resource for an understanding of API calls, enabling you to seamlessly implement the process of adding groups in the context of SAML JIT with this Blog here. Join us as we bridge the gap between theory and practice, empowering you to optimize your Workspace ONE Access experience effortlessly.
You can start by creating your SAML IDP in Workspace ONE Access in the GUI. Once done make sure you have JIT enabled in the federated SAML IDP and a Directory name selected:
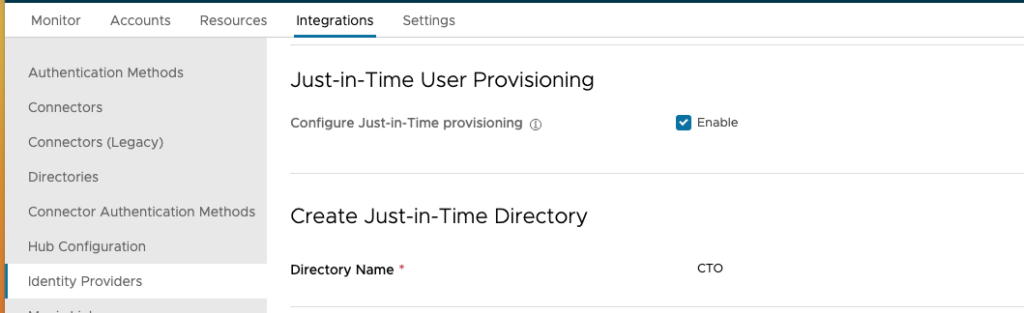
Now if we would use this IDP Users would be added , but no groups, so let us start using the API to enable Groups.
Get list of all federated IDPs via API
To get a list of all SAML IDPs we just run the following command via API.
GET https://{{Access}}/federation/identityproviders/ I use Postman, hence I added the scrteenshots of Postman here as well with my settings:
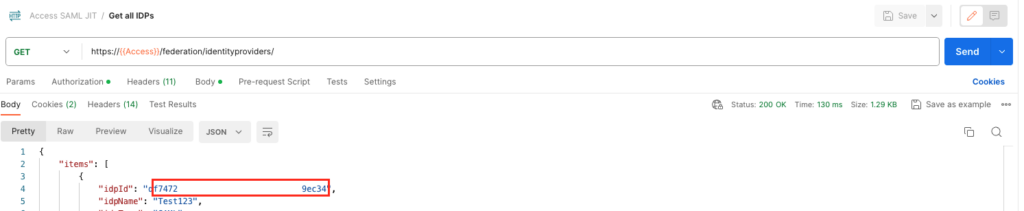
Make sure you copy out the “idpID” of the correct SAML IDP to then run the next API Calls.
Get Details of the Federated IDP via API
now add the “idpIT” to the API Call and run it to get the current settings of the IDP:
GET https://{{Access}}/federation/identityproviders/{{IDP}}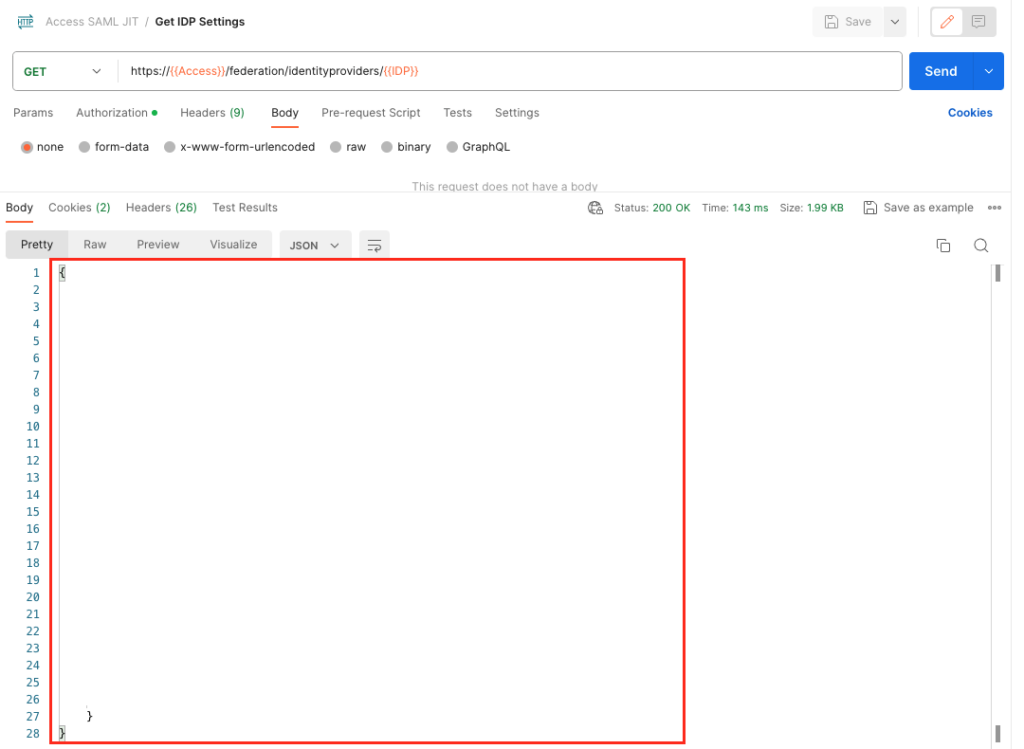
Once you see the result , Copy this out and put it to the Body of the next “PUT” request
Update IDP to Enable Group Provisioning
Now you can Update the Request to PUT instead of GET and also add in the Header the Content Type “application/vnd.vmware.vidm.federation.samlidentityprovider+json”
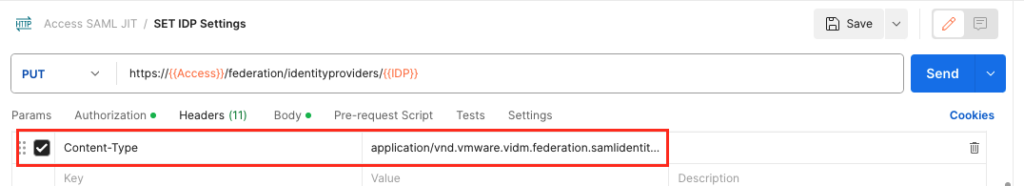
Also make sure the Body is set to “raw” and JSON and copy in the Result from the previous API Call.
Add after the “requestnameIdFormatType” the following code, while the “Groups” need to match the Attribute where the Group memberships are included:
"jitGroupMembershipAttrName": "Groups",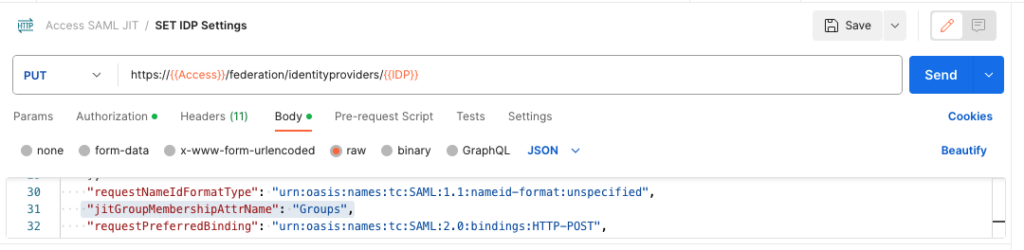
then Send the API Call and make sure it is successful.
Once done you can also verify that the settings are there with a “GET” API Call:
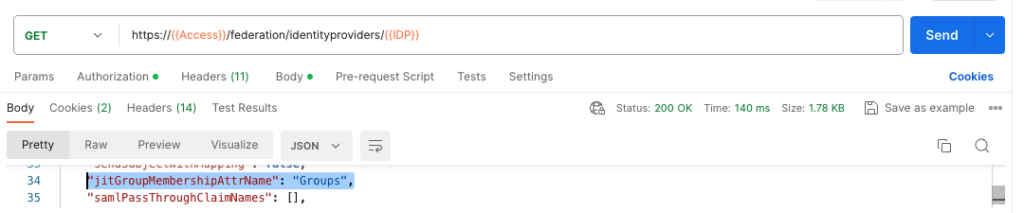
Conclusion
Now once new Users login with the federated IDP the users will be created including the Groups and users will be member of the groups they belong to. Also AirWatch Provisioning App Can be used to get users and Groups to UEM. I tested and verified this with Google as IDP and with Workspace ONE Access SaaS in November 2023.
Used API Calls can be imported via Postman from my GitHub repository : https://github.com/EUCPatrick/UEM-API-/blob/main/WS1%20Access%20SAML%20Group%20JIT.postman_collection.json
vExpert, blogger and VMware & Omnissa champion. Worked 10 years as a Architect for a partner before joining VMware in 2017. Moved to Omnissa in 2024.