Bringing Workspace ONE Mobile Threat Defense to the next Level with integrated Safe Browsing (aka. Phishing & Content Protection)
January 2025 Update: Updated to new Omnissa Tunnel App IDs and Screenshot
More and more Phishing attacks happen out side of corporate mail, So to prevent them a Phishing and Content Protection is a good option. As Omnissa is offering a Add-On for the UEM Installations , let us have a look on the latest and greatest that went GA in June.
Due to some operation system platform limitations you only can have Phishing & Content Protection (PCP) or a VPN if you go with the Lookout for Work App. But now with the integration of Hub and Tunnel App it brings this to a new level. So Mobile SSO, VPN and Phishing & Content Protection on the same Device without any issues. This really brings the Deployment to a totally new Level.
Pre-Reqs:
This Blog assumes a Customer that is already enabled with MTD and also has die the Hub MTD activation via the SDK Settings. If you have not done it yet, it is just adding 2 lines of config to the UEM Console , but I will not do into detail here as there are some TechZone articles already there that cover it in details.
To enable this features there are some pre-reqs required listed here:
- Hub Version iOS 23.05 or Android 23.05 or higher
- Tunnel Version: iOS 23.01.1 or Android 23.01 or higher
- Active Omnissa Mobile Threat Defense tenant.
Configuration for in the MTD Console
Note: Assumption here is you have already MTD activated with Omnissa via the SDK Settings and just want to add PCP.
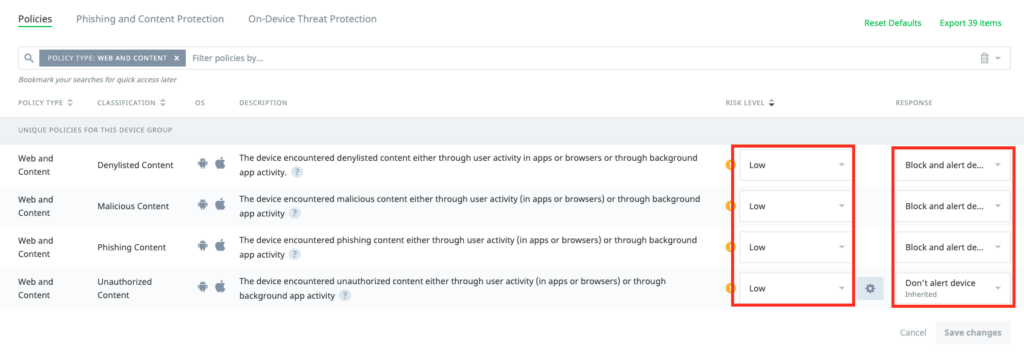
Go to the “Protections” and click to the “Phishing and Content Protection” for you Device Group.
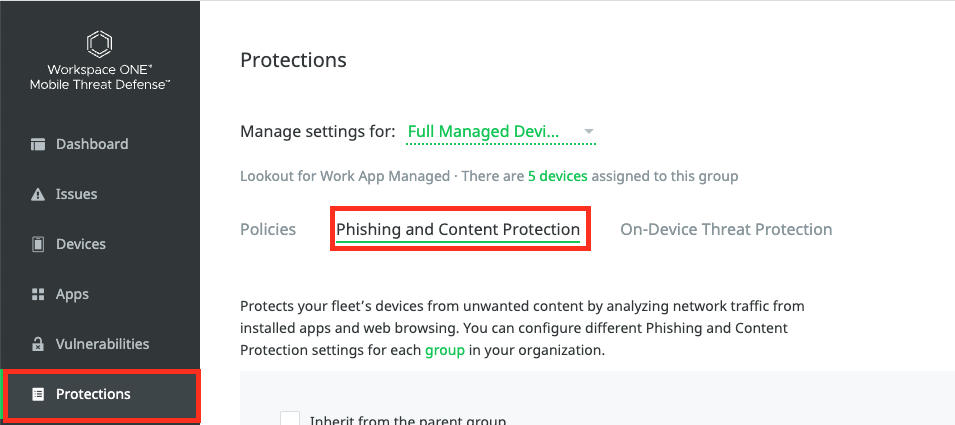
Once there make sure you enable the Phishing and Content Protection and then Select “Secure DNS” only. If you want to enforce it enable the “Mandatory” Setting, so the user does not have the choice to enable / disable it.
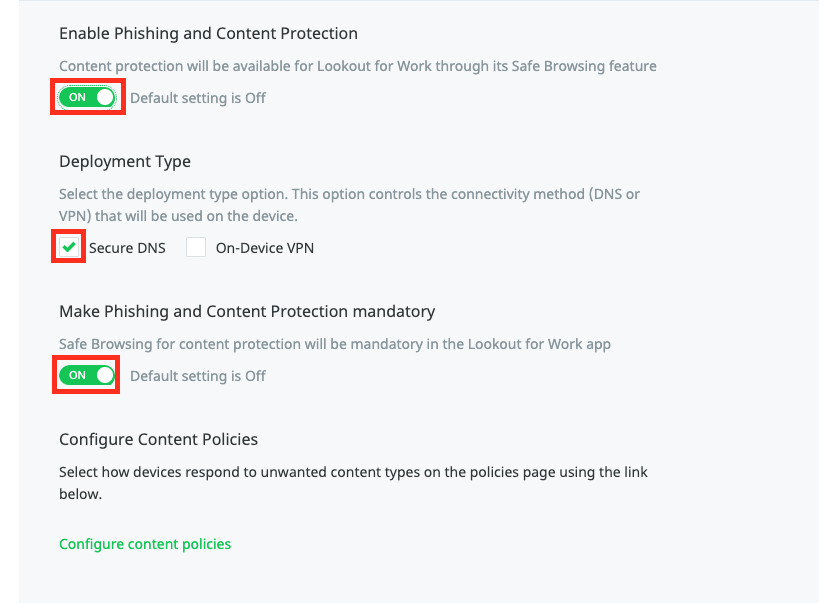
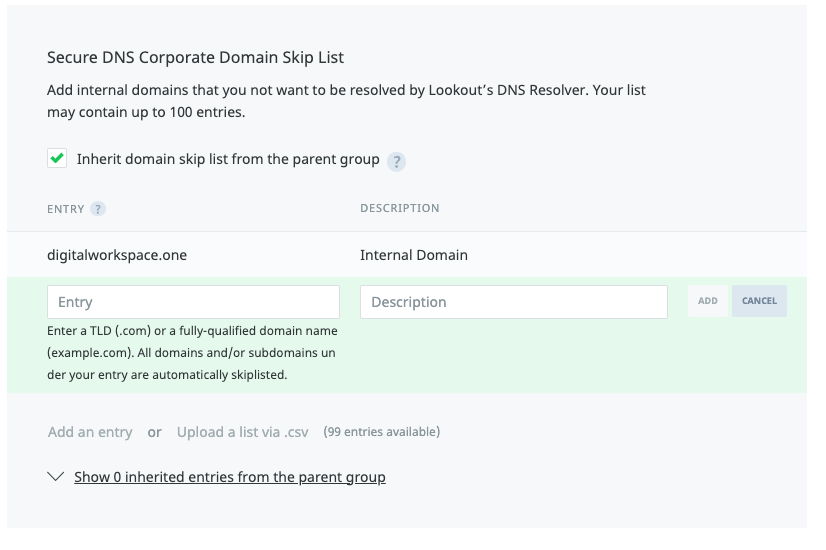
If you use VPN and you access internal Domains, make sure you add the Tunnel URLs to the “Skip List” for the Domains that are not public reachable.
once done “Save” the settings and click to “Configure content policies”
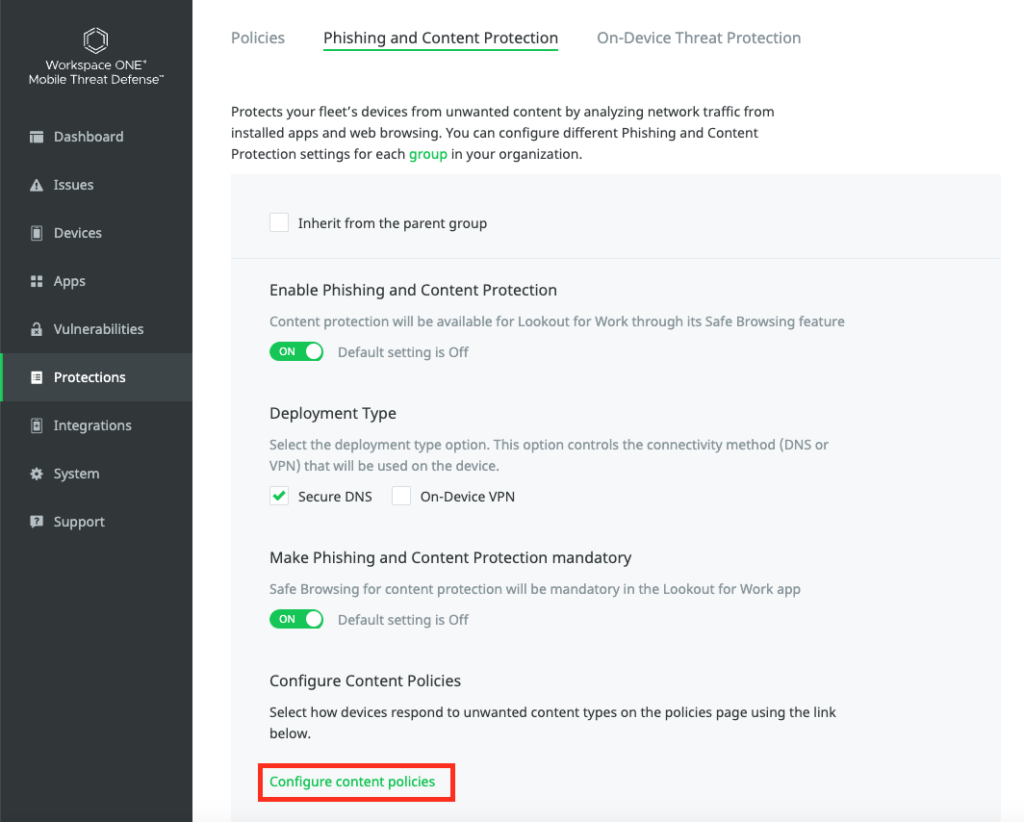
Here the policies and the Risk Level can be set. Also ensure the “Block & Alert” is set, as otherwise the Phishing pages will not be blocked.
To provide a better overview I created a Video , so it is easier to follow the above steps:
With all that, we have the MTD Console Config done and can done the configurations for iOS and Android next.
Configuration for Android
For Android the Configurations are really simple. Make sure you have the latest and supported Hub Version and Tunnel Version installed and the Custom Settings to activate MTD are set in the UEM console. once done you can test everything out.
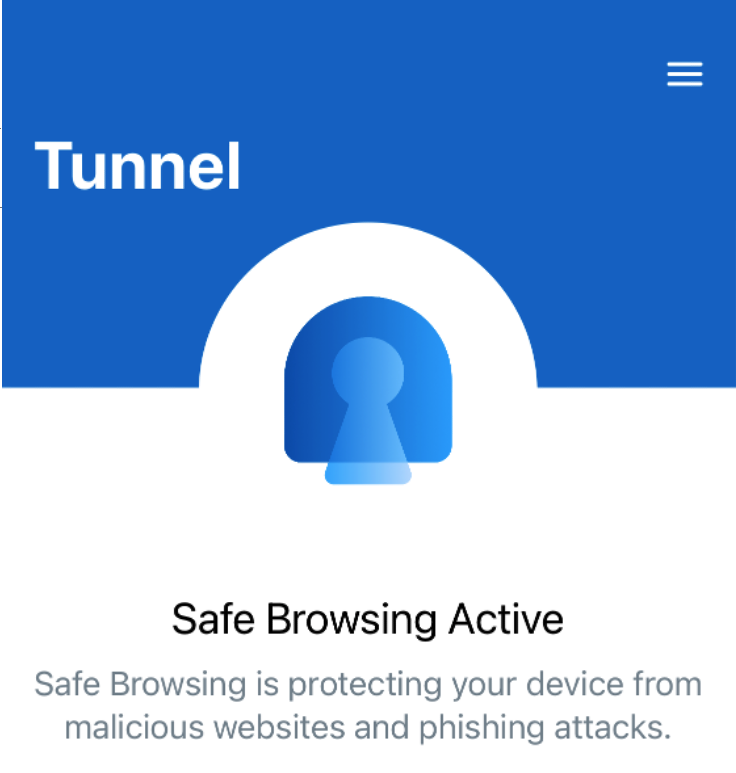
If you go on the Device now the Tunnel App the SDK gets enabled and it fetches the Secure Browsing :
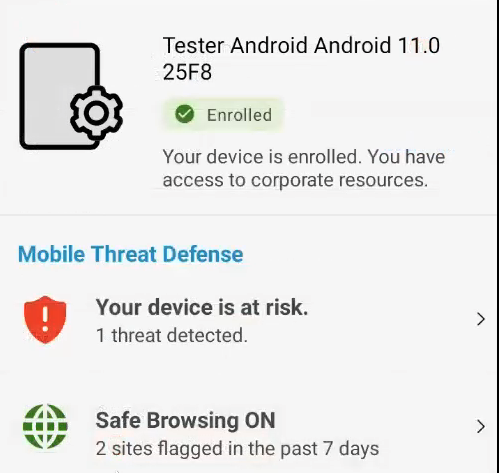
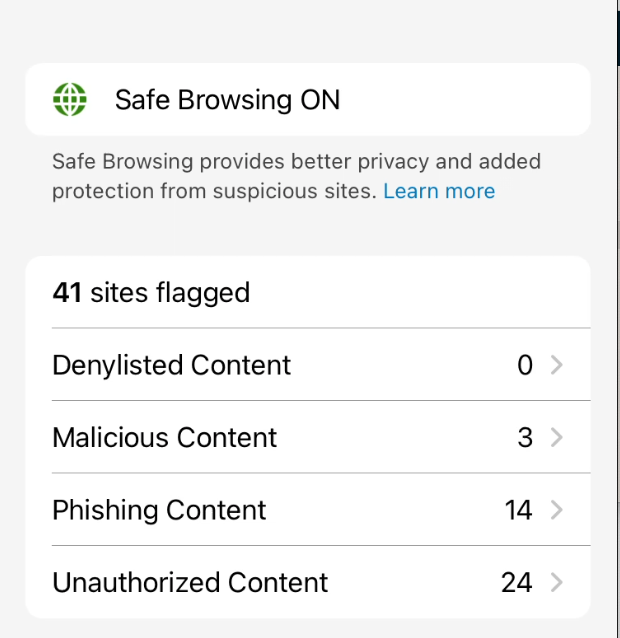
In Android Intelligent Hub you can see that Safe Browsing in the Support Tab is also enabled and you can get some details as User as well.
Configuration for iOS
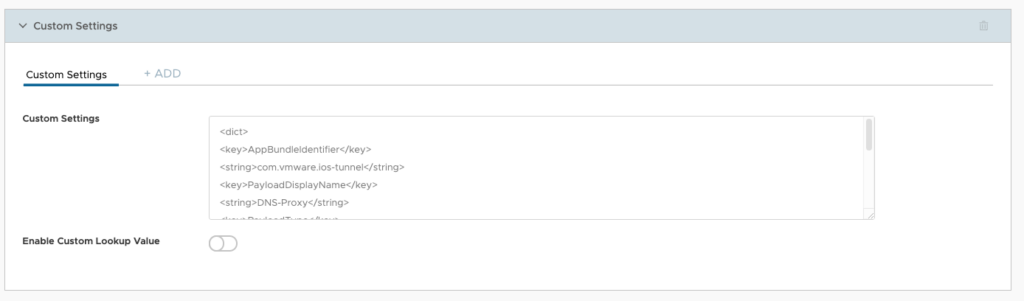
For iOS we need to create a Profile for the DNS if there is no Omnissa Tunnel Profile set. If you use a Omnissa Tunnel VPN Profile , just ignore this custom Profile. Therefore create a new Device Profile for iOS and add the Custom XML shown here:
Note: With the new Omnissa Branding the App ID of Tunnel changed: See Details Here: https://kb.omnissa.com/s/article/6000684?lang=en_US
<dict>
<key>AppBundleIdentifier</key>
<string>com.ws1.ios-tunnel</string>
<key>PayloadDisplayName</key>
<string>DNS-Proxy</string>
<key>PayloadType</key>
<string>com.apple.dnsProxy.managed</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>PayloadIdentifier</key>
<string>com.apple.dnsProxy.managed.41CB9A8F-3324-4F97-8C4A-7746E835045F</string>
<key>PayloadUUID</key>
<string>41CB9A8F-3324-4F97-8C4A-7746E835045F</string>
</dict>Once added it should look like this, so make sure the Profile is assigned to the Fleet of iOS Devices with the Assignment Type set to “Auto”.
For iOS there is just this little profile extra, which makes the Configurations are really simple. Make sure you have the latest and supported Hub Version and Tunnel Version installed and the Custom Settings to activate MTD are set in the UEM console. Once done you can test everything out.
If you open now Tunnel it will activate the SDK and look similar to this:
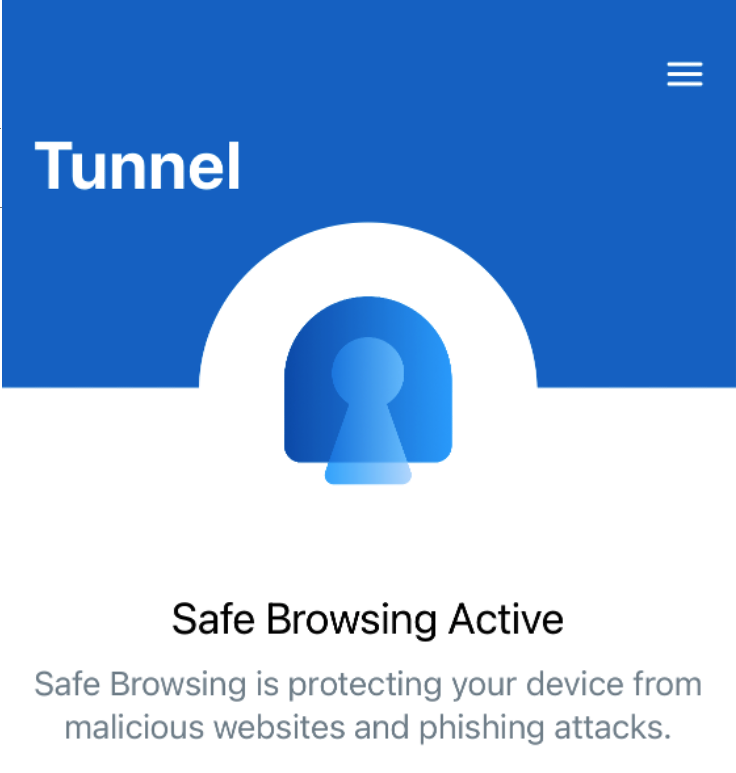
Within the Omnissa Workspace ONE Intelligent Hub you will see the Secure Browsing is “ON” and if there are detected URLs you will see them and can have a deeper look as User as well. Also the Admin gets this URLs listed in the MTD Console.
To create a better overview I created a Video with the UEM Console Settings used:
Admin Experience :
Reporting can be used in Mobile Threat Defence Console as well and we see the URL that was blocked and all the classification of the Content:
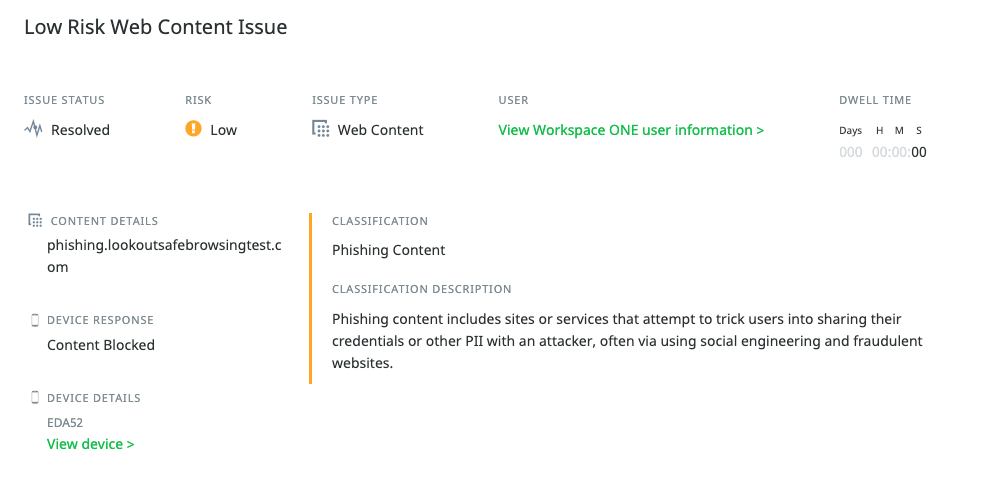
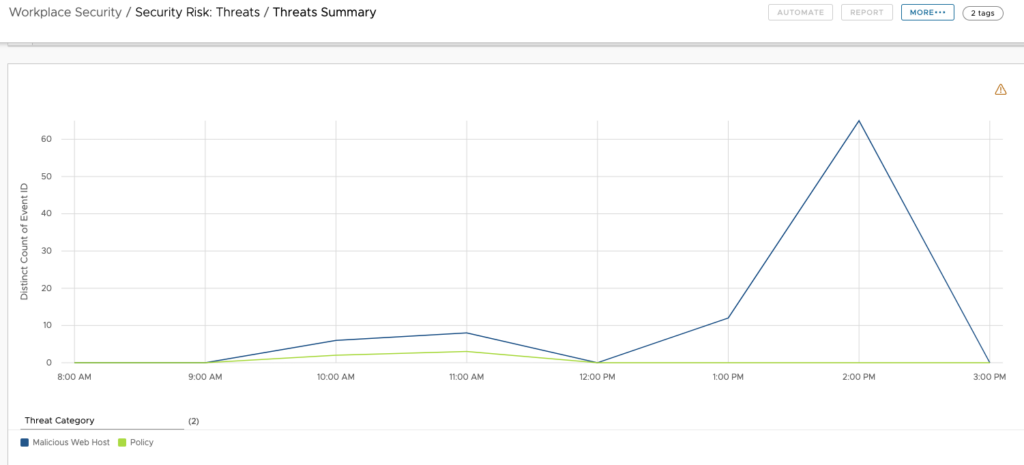
This data can also be used with Workspace ONE Intelligence to build Automations or Dashboards to get a better view of the whole fleet and trends.
Device Demo
In this section of the Blog I want to show the device experience of MTD with PCP enabled. Here a demo of iOS :
also here the Android Device Demo :
Conclusion
Now we have successful deployed Mobile Threat Defense incl. Safe Browsing (aka. Phishing and Content Protection) for Workspace ONE UEM managed devices on iOS & Android. Tested it on iOS and Android and see all the Events in the MTD Console / in Intelligence. This brings the Security on the Device to the next Level, while keeping things as simple as possible for the User and the Administrators.
Note: This Blog was published at the GA of the feature , while the Demos and Videos have been recorded at the Beta Phase in Early 2023.
vExpert, blogger and VMware & Omnissa champion. Worked 10 years as a Architect for a partner before joining VMware in 2017. Moved to Omnissa in 2024.
Francesco
Hi Patrick! Thanks for the guide!
Can you tell me how you managed to configure the “View Workspace ONE user information” item in the device details? In my console I don’t have any reference to the device, and therefore I can’t understand which device it is and which user it is associated with…
Thanks a lot!
Francesco
Patrick Zoeller
on a Omnissa MTD Tenant this should be on by Default.
Make sure you have the UEM Integration via API done correctly and also that them “Omnissa MTD” logo is in the left corner and not the Lookout Logo.
If it is the lookout Logo , you can reach out to Lookout Support and ask them to not Store the Username/ Mailadress as they have this feature behind a FF by Default.
Best regards
Patrick
Francesco
Our console has the “Workspace ONE Mobile Threat Defense” logo in the top right, but the URL is “https://mtp-euc1.lookout.com/”.
API integration is configured as each new device enrolled in Workspace ONE UEM also appears in MTD.
Maybe we need to enable the “Automatically drive Lookout for Work enrollment on Workspace ONE managed devices” feature in Integrations > Enrollment Management ?
We have not enabled this section because the enrollment still occurs automatically via the settings in “Connector Settings”..
Patrick Zoeller
Yes , you need to Enable the setting in the “Enrollment Management” so it get the Device IDs and can match them.
Francesco
Hi Patrick, thanks a lot for your support.
now I was able to see all the users.
Now another problem has arisen with iOS devices:
After having followed the steps of the procedure and correctly activated Safe Browsing, I can still access all the sites, even those considered phishing or unauthorized. And no notification of blocked content appears.
However, for Android devices everything works correctly, the sites are blocked and the devices alerted.
Do you have any suggestions?
Thanks!
Francesco
Patrick Zoeller
Hi Francesco ,
Make sure that the Profile for iOS is installed on the Devices to move the DNS to the Tunnel Client.
best regards
Patrick
Michael
Hi Patrick,
I am really enjoying your blog as source of information. Last week we got finally access to our MTD console and I integrated the MTD console with our on-prem Workspace ONE, everything works great.
As soon as I put some specific devices in a dedicated smartgroup in the linked OG I see the devices synced in the MTD console, so far so good. But they are always in the “pending” state, I also do not see anything MTD related inside the Intelligent hub (Device got enrolled before MTD integration). Just for a test I downloaded the lookout for work app and entered the activation code and just as I did this the device gets the “safed” status in MTD and also the policies I have configured so far are working fine.
BUT as far as I understand the lookout for work app should not be necessary and everything should be integrated in Hub, right? Or did I get somethjing wrong here? Also the endusers should get activated automatically without enering any code right?
I pasted the JSON to “Groups & Settings > All Settings > Apps > Settings and Policies > Settings” for activating MTD but it seems not have any affect on my test devices, did I something wrong or do I miss something?
Patrick Zoeller
Hi Michael ,
So it looks like you have the correct settings on the Lookout Side, but on the UEM Side there seems to be some wrong things. Make sure you have the Activation code added in the Settings and the MTD is activate.
This seems to not be the case. Make sure that Hub uses the Default SDK Profile or update the other profile with the Settings.
Best regards,
Patrick