Block TikTok with Workspace ONE on iOS
With different government bodies as well companies moving to block TikTok a lot of question are being raised on how to achieve it. This article aim to list all the method possible with the Workspace ONE platform.
Privacy
While we all aim to address the issue and sort everything out quickly, it is necessary to review the privacy policy.
In order for Workspace ONE UEM to take action, it needs to know that the application is installed on the device which means capturing the data on personal applications.
Depending on the IT policy as well as the privacy law this might be difficult, always align with the privacy policy of the country where the user is attached to. Also, capturing personal application, can reveal personal details, for example, a user have pregnancy app or an app talking about cancer and you know from the application name some context of the user.
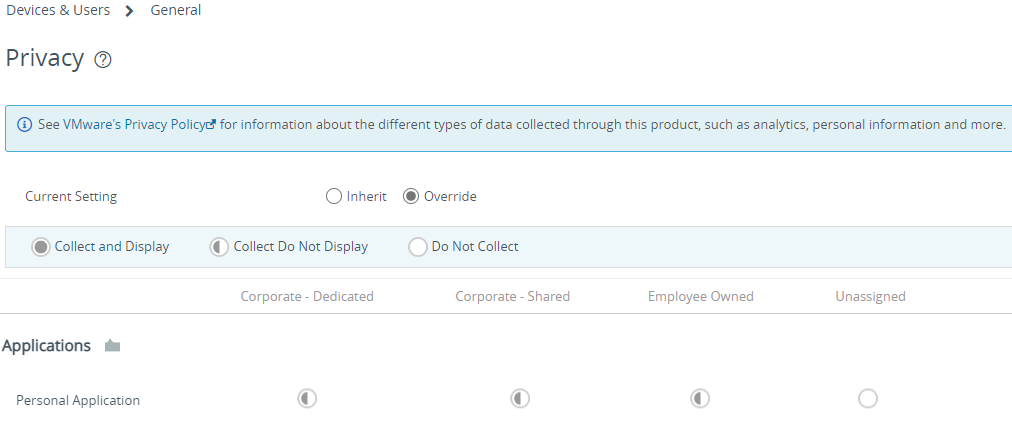
In Workspace ONE UEM, the privacy settings are set across 4 devices type: Corporate Dedicated, Corporate Shared, Employee owned and unassigned, it is very important that the devices are categorized properly within the console also Workspace ONE UEM separate corporate applications and personal application.
The recommandation is to collect but do not display the information to the administrator which allow Workspace ONE to act but without the administrator knowing what are the other applications on the device.
User enrollment
User enrollment is an enrollment mode allowing a separation of corporate data on a personally owned devices. Apple creates a dedicated volume within the device to store the corporate data. iOS and iPadOS do not allow access the inventory of personal data as well as control over it therefore Workspace ONE UEM cannot take action or alert administrator that the device have the application installed.
More info : User Enrolment and MDM
Unsupervised devices
Unsupervised devices are less and less common due to Apple deprecating MDM api and adding more API on the supervised devices side. However some control can be achieved, the first control is compliance.
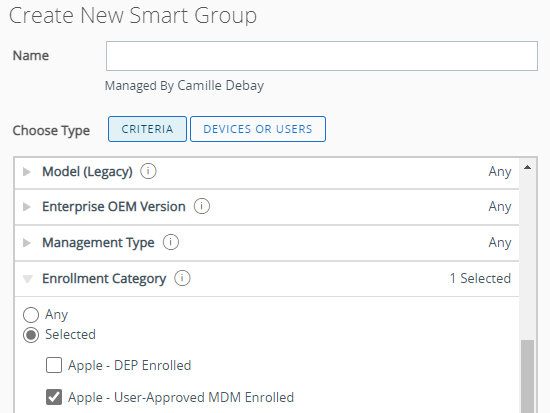
To target unsupervised device you can create a smart group with the Enrollment Category filter at Apple – User-Approved MDM enrolled.
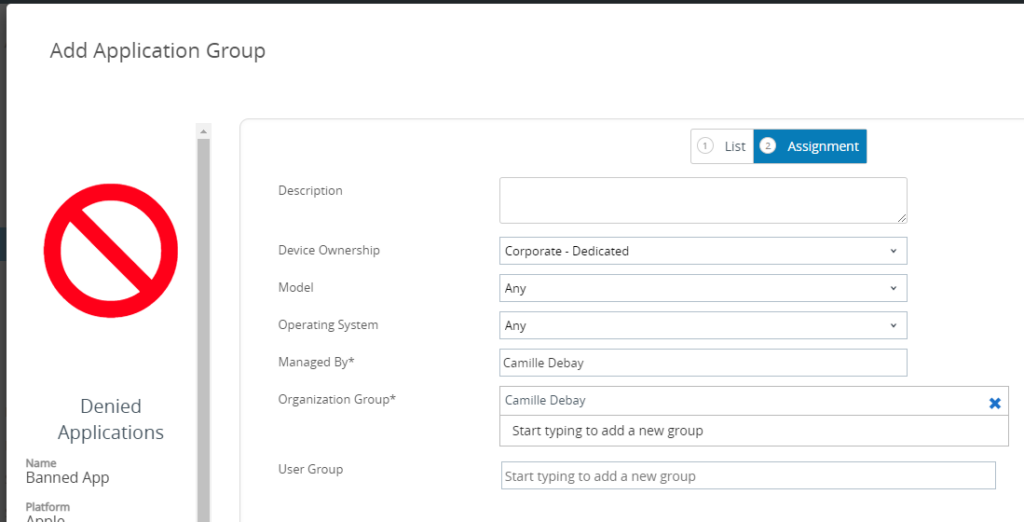
Application Group
If multiple application need to be monitored an application group can be created.
Go to the App Group list view then click on Add Group
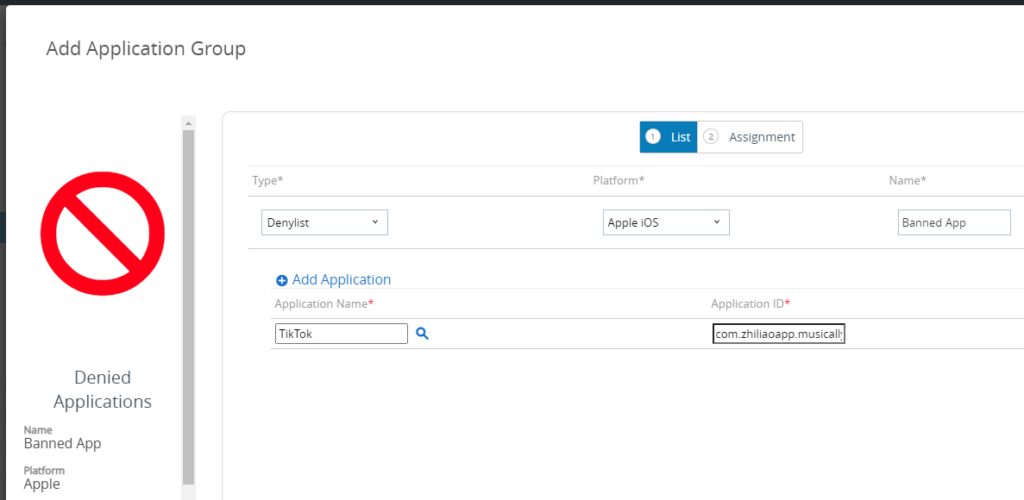
Select Denylist, select iOS for the platform give it a name. In application name put TikTok, does not have to be the exact name, the Application ID the attribute used for matching. Use the application ID
com.zhiliaoapp.musicallyTips: You can use click on the blue magnifier to search in the store and it will pull the corresponding application ID.
Assign it to the targeted user.
Compliance
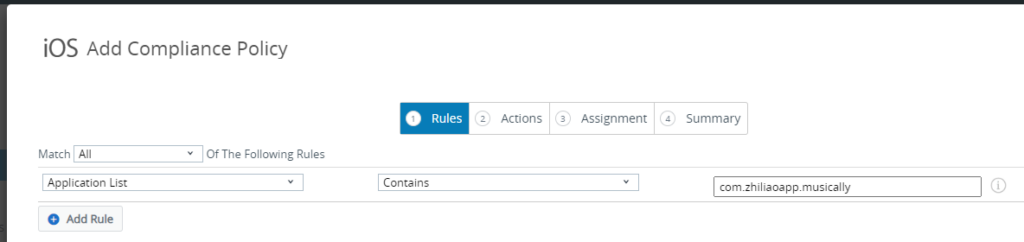
To create a compliance, go to Compliance Policies list view and click on Add.
Select Application List then Contains and use the following Application Identifier
com.zhiliaoapp.musicallyTips: if multiple application needs to be denied, you can use Denied Application Group created earlier and then select Contains Denied App(s) in the compliance policy.
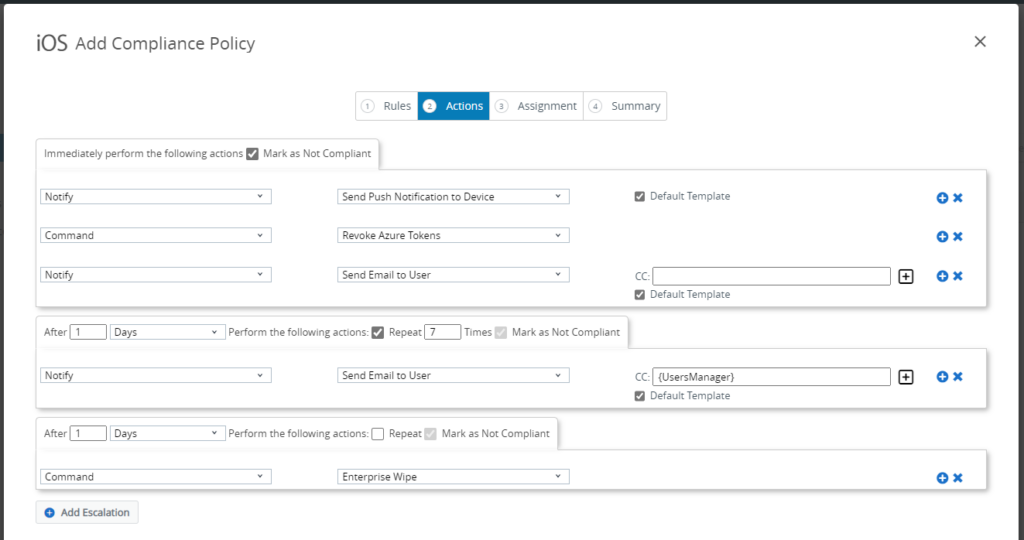
In the Actions section, choose the escalation path to notify the user.
In this example, we are notifying the user with a Push Notification and an email as well as revoking the Azure AD token which will enforce the user to reauthenticate across the devices then 1 days later for 7 days an email is sent to the user with the manager in copy, user manager need to be synced as an attribute in UEM in order to be able to use it. After this an Enterprise Wipe is executed on the device.
Assign to the targeted users.
Supervised devices
For supervised devices, the first solution is to disable the app store and only publish approved apps using VPP Device based deployment.
Restrict App Store access
To restrict the app store you deploy the setting by tick Restricted Mode for Public iOS Applications in All settings > Apps > Workspace ONE > App Restrictions.
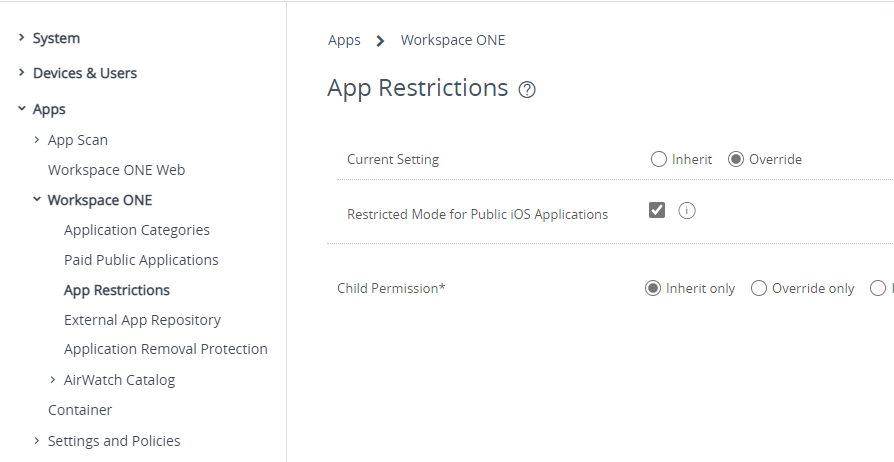
App Store enabled
While restricting the usage of the app store is an easy fix, this might not be a solution for everyone. In that case, it is possible to denied applications to run as well as taking over and forcing removal of the application.
To do this we need to, at high level:
- Create a restriction profile
- Assign to smart group with a tag
- Adding the denied app as a VPP app
- Tag device with Workspace ONE intelligence
In this scenario, compliance can also be used to warn the user follow the steps in the unsupervised section for doing so.
Restriction profile
Create an iOS profile and select Restrictions, depending on the console version click on Add or Configure
If you clicked on Add then click on the Applications tab
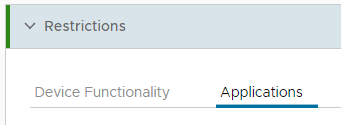
Scroll down to the Hide Apps section
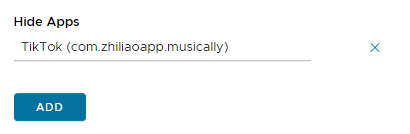
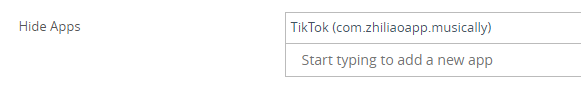
Note: Hide Apps in the console is using the following MDM restriction on iOS blockedAppBundleID, when this restriction is used the following happens:
If present, prevents bundle IDs listed in the array from being shown or launchable. Include the value com.apple.webapp to restrict all webclips. Note that denying system apps may disable other functionality. For example, denying the App Store app may prevent users from accepting the terms and conditions for user-based VPP.
Requires a supervised device. Available in iOS 9.3 and later, and tvOS 11.0 and later.
Source: Restrictions | Apple Developer Documentation
The Hide Apps completely block the usage and background refresh of the application we now need to remove it.
Create smart group with a tag
To create the tag go to All Settings > Devices & Users > Advanced > Tags then click on Create tag
Now, we need to create the Smart Group with the Tag filter at the tag we just created.
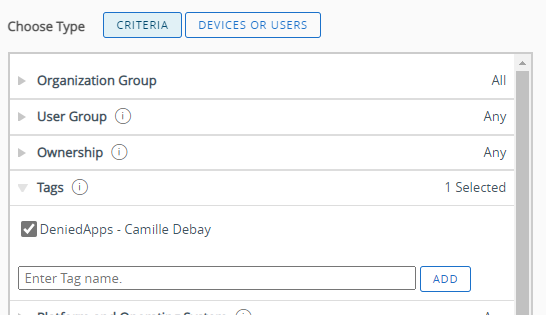
Add the denied app to VPP
Connect to Apple Business Manager, click on Apps and Books, search for TikTok and assign it to the correct location.
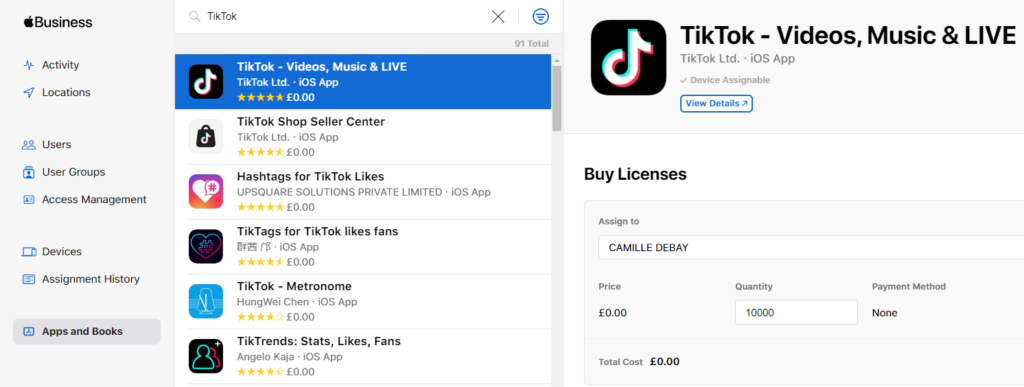
Once the order is processed by Apple, head to the Workspace ONE UEM console.
Go to the Applications list view, click on the Purchased tab then click on Sync Assets, this will enforce a sync with Apple to get the latest licenses without waiting.
Once TikTok appears in the list select it, click on More action then click on Enable Device Assignment
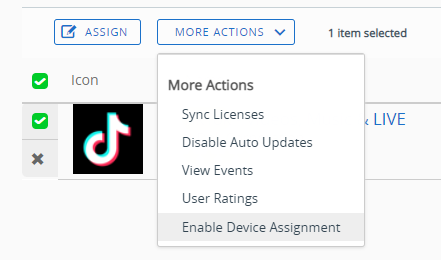
Click on OK
Once done, click on Assign
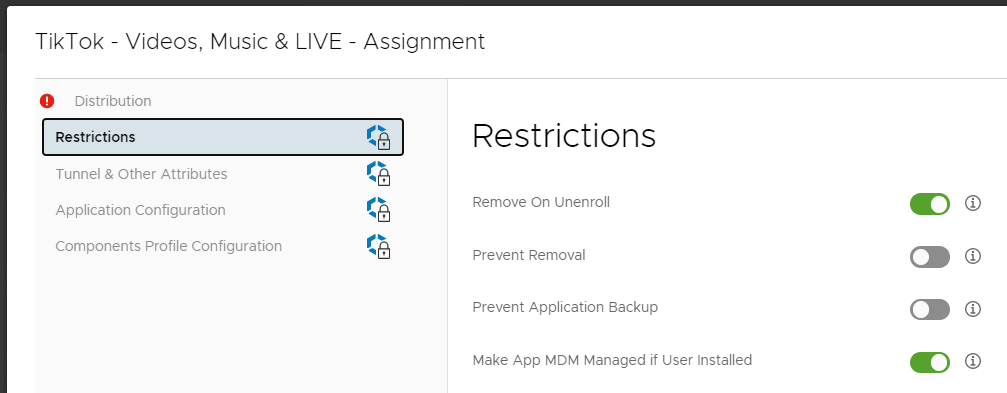
Click on Restrictions on the left hand side then toggle Make App MDM Managed if User Installed
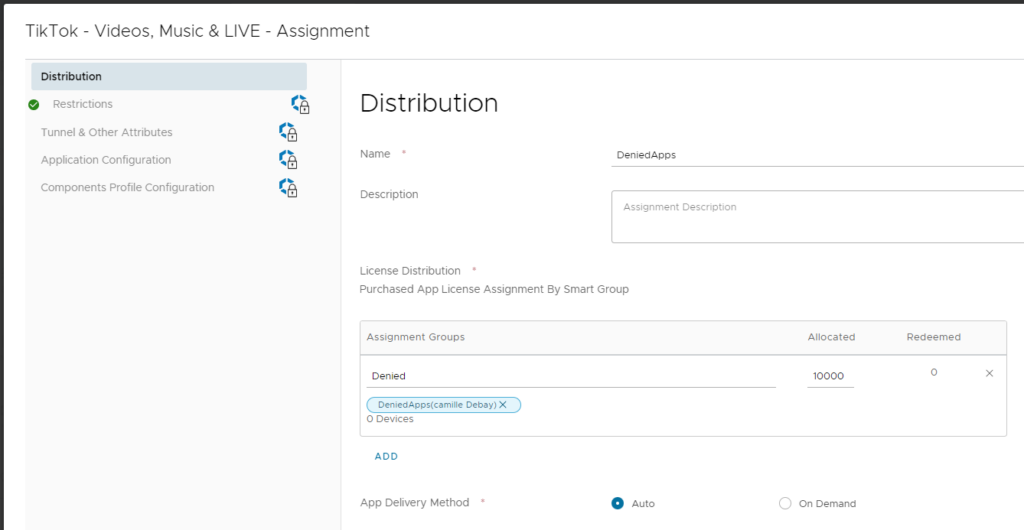
Click on Distribution, select Auto for App Delivery Method, select the smart group created earlier and allocate enough licenses. Click on Create, then Save, and finally Publish
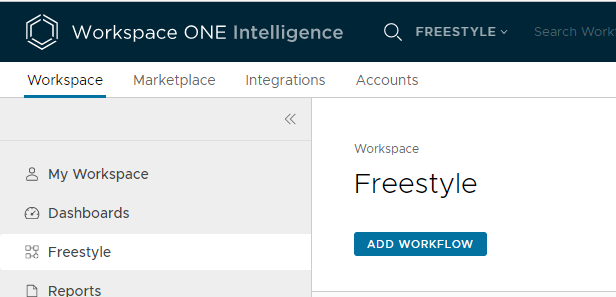
Tag the device with Workspace ONE Intelligence
Head to Workspace ONE Intelligence, in the Workspace tab, click on Freestyle, then click on Add Workflow
For Data Source, select Workspace ONE UEM then Apps
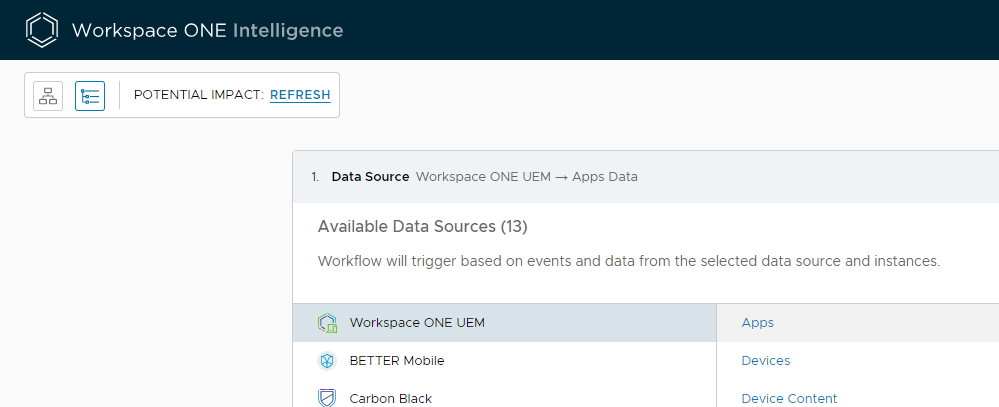
The trigger should be Automatic
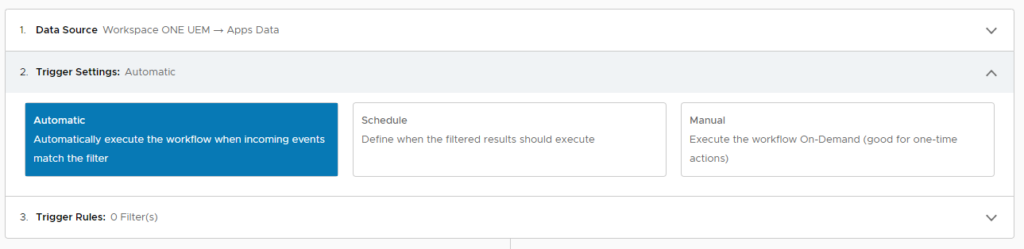
Add a filter with the App Identifier equals com.zhiliaoapp.musically
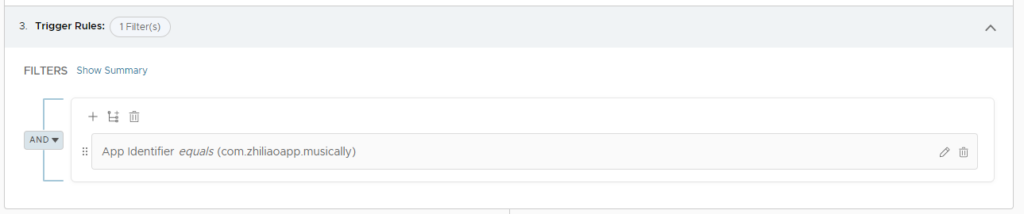
Click on Add Action then select Workspace ONE UEM
Select Add Tag to Device then click on Add Action
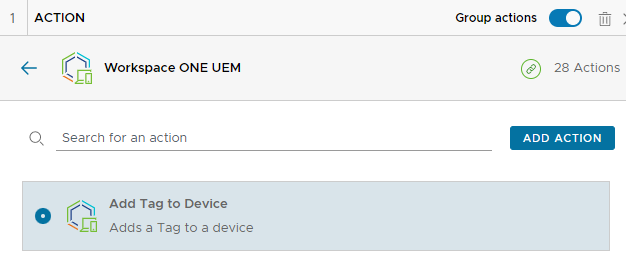
Search for the tag in the OG where it was created
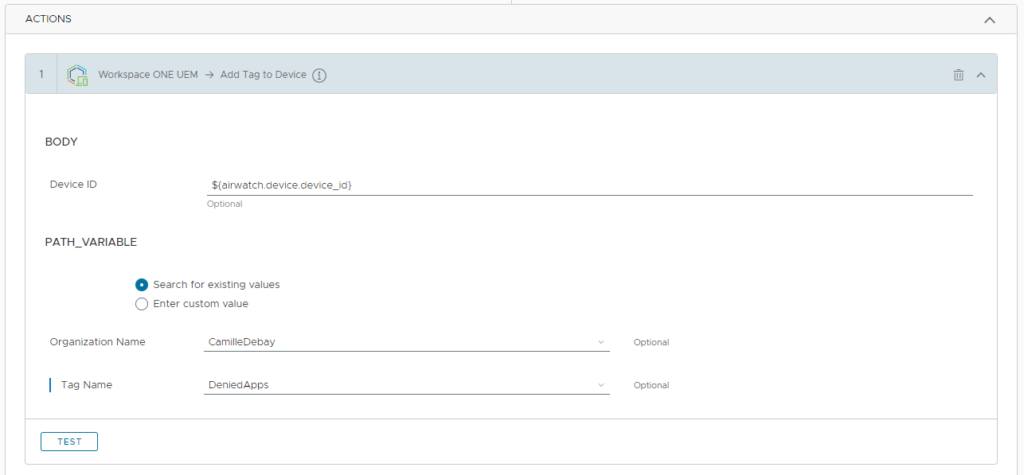
Add another action to Sync the device
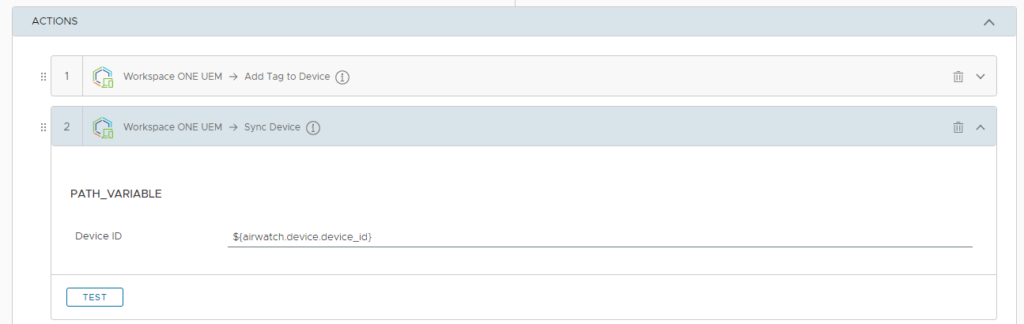
Add the action to Remove Purchased Application and search for TikTok.
Give the workflow a name and enable it.
Remove the tag
Once the application has been deleted we need to remove the tag. To do so we need to create a new workflow same as adding the tag but with the filter at Does Not Include the TikTok app identifier and that the Device have the tag assigned.
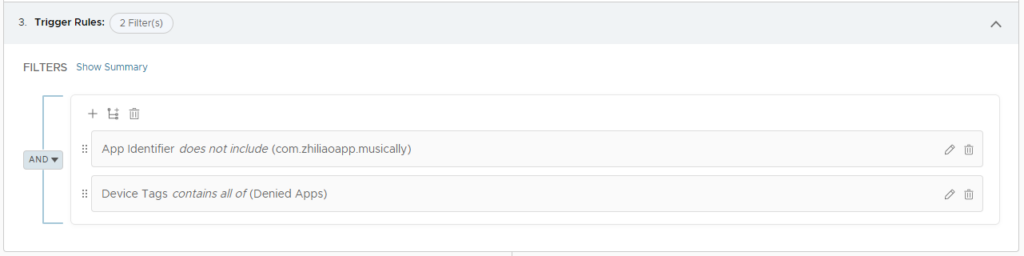
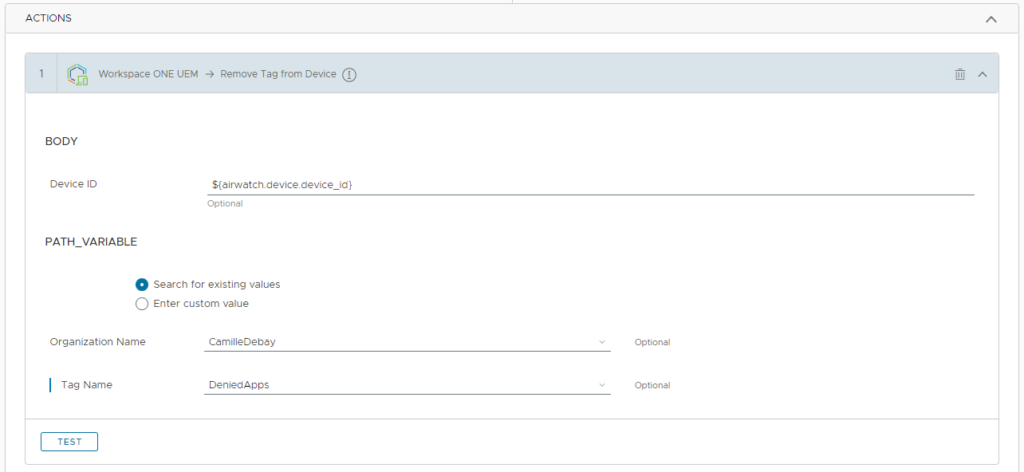
The action for the workflow is Remove Tag from Device
vExpert, blogger and VMware champion. Worked as a Microsoft consultant for a partner before joining VMware via Airwatch in 2015.
Kenny-Lee
Very complete guide, thanks Camille! In essence for BYOD/COPE (MDM profile enrolled) we don’t have full control, as we shouldn’t, and press the user to resolve the issue by notifications, blocking specific services up until wiping all work data. Whilst on COPE/COBO (supervised enrolled) we have more control and can make any app managed without user interaction which lets us ensure removal.