Hybrid Modern Authentication with Omnissa Boxer – Part 1 – Introduction
To improve readability and comprehension the subject is divided in multiple articles:
- Part 1: Introduction
- Part 2: Prerequisites
- Part 3: Configuration
- Part 4: Special use cases and FAQ
- Part 5: Troubleshooting
What is Hybrid Modern Authentication?
Hybrid Modern Authentication (HMA) is Modern Authentication applied to Microsoft Exchange on-premises. This allows organizations to use Azure authentication, whether it is federation with a third party IDP or directly with Azure for managed domains, for their on-premises Microsoft Exchange.
The common authentication method allow uniformity in the authentication process, conditional access, and simplicity of configuration between on-premises users and cloud users.
Why Omnissa Boxer over Microsoft Outlook?
Currently, Microsoft Outlook for iOS and Android uses MS Sync to communicate, this protocol is only supported by Office 365 which means that to access on-premises mailboxes, Office 365 need to proxy the ActiveSync protocol then translate to Outlook. By doing so Outlook have a long list of limitation and unsupported features:
- Draft folder and Draft messages synchronization
- Viewing more than four weeks of email by using the “Load More Messages” link at the bottom of the message list
- Shared calendar access and delegate calendar access
- Shared and delegate mailbox data access
- Cortana Time to Leave / Travel Time
- Rich meeting locations
- Task management with Microsoft To Do
- Add-ins
- Interesting Calendars
- Play My Emails
- Sensitivity labelling
- S/MIME
Omnissa Boxer on the other hand uses ActiveSync protocol and direct access to the on-premises organization so it does not have these limitations.
All regular Omnissa Boxer features are supported with Hybrid Modern Authentication the same way as with Modern Authentication with Office 365.
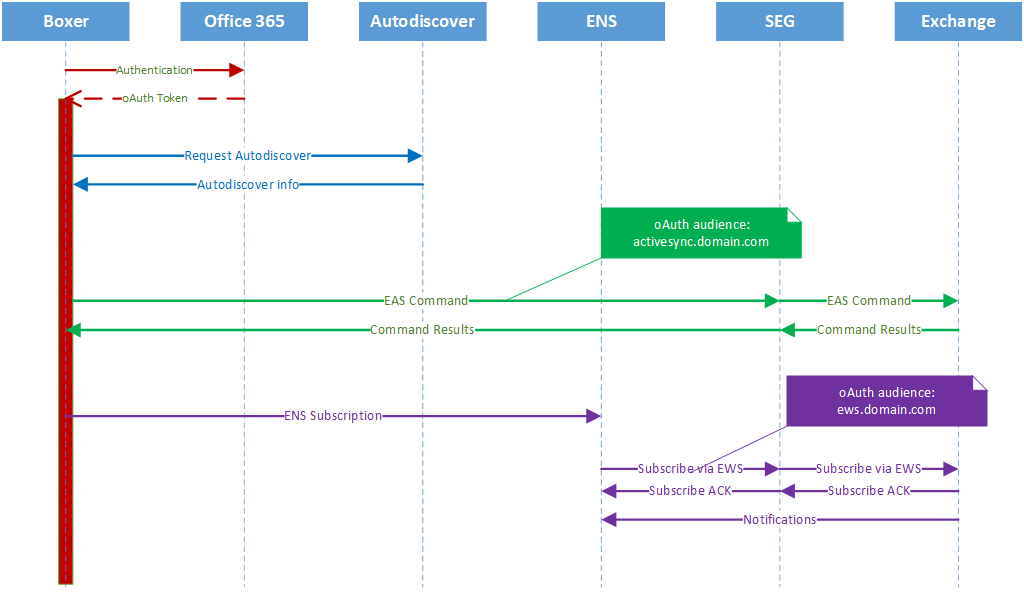
How does it work?
User Flow
The user authentication is the same as any other Modern Authentication flow.
Server side
Hybrid Modern Authentication uses oAuth protocol to establish a trust between the on-premises exchange organization and the Azure cloud.
Authentication Server
The authentication server is responsible to authenticate the user and the issuer to deliver the oAuth token. In the case of the Hybrid Modern Auth oAuth endpoints are:
- Authorization endpoint: https://login.microsoftonline.com/common/oauth2/authorize
- Issuer endpoint: https://sts.windows.net/<Azure AD GUID>/
Audience
Audience in oAuth is using the same principle as in the SAML protocol or Kerberos, it’s the destination name for where the token will be used.
Example:
- ActiveSync URL: https://activesync.domain.com/Microsoft-Server-ActiveSync
- Token Audience : https://activesync.domain.com
- Exchange WebService URL: https://ews.domain.com/EWS/Exchange.asmx
- Token Audience: https://ews.domain.com
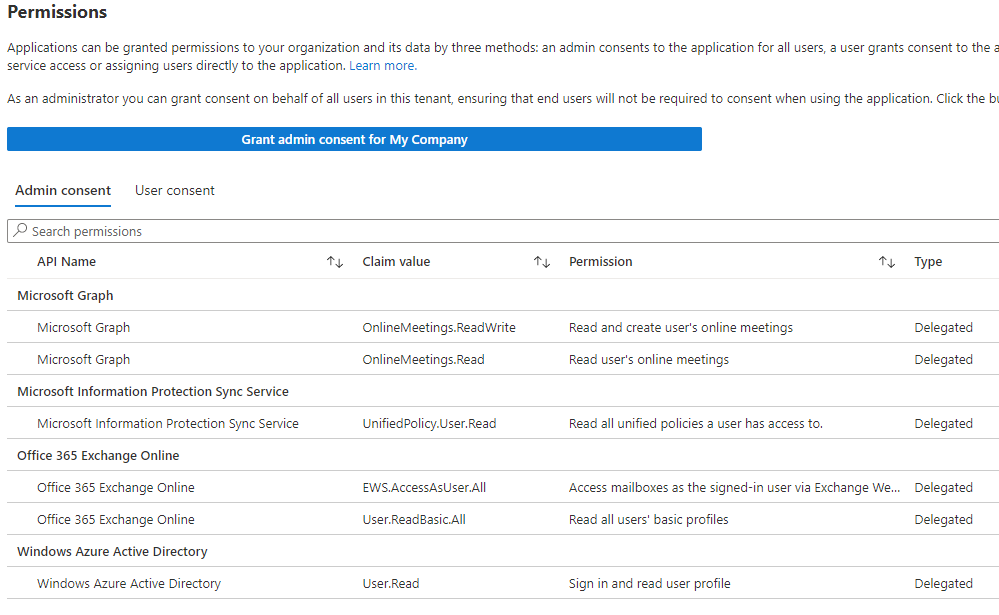
Scope
Scope is what limit the token can do for Omnissa Boxer, we have following permission granted for delegation
Validation
The validation of the oAuth token is done by the Exchange server itself using the setting of the virtual directory attached to the service.
It is using the URL setting to do this validation and comparing it with the http request it is receiving. As this validation is done at the Exchange server level, you cannot use different FDQN name between the access and the configuration, for example:
Used on the email client: https://seg.domain.com/Microsoft-Server-ActiveSync
Exchange Virtual Directory External URL Parameter: https://activesync.domain.com/Microsoft-Server-ActiveSync
When the email client will request authenticate and get a token to access the ActiveSync endpoint, as it knows only seg.domain.com, it will request a token for that audience. When the token arrives on the Exchange server, it validates the token against its parameters and invalidate that token as it is not matching what the server has on record therefor denying the authentication request.
The following error can be seen in the Exchange logs:
Microsoft.Exchange.Security.OAuth.InvalidOAuthTokenException:
The hostname component of the audience claim value ''https://seg.domain.com'' is invalidIf want to know more with a deep dive read this article from the Microsoft Exchange Team at Microsoft:
Deep Dive: How Hybrid Authentication Really Works – Microsoft Community Hub
Next: Part 2 – Prerequisites
vExpert, blogger and VMware champion. Worked as a Microsoft consultant for a partner before joining VMware via Airwatch in 2015.