How to get Secure Email Gateway with Multi Datacenter in a Active – Active Mode with Clustering
While Secure Email Gateway (SEG) is used at multiple organisations and is available on Windows or as part of the UAG , there can be some caveats in complex Environments. If you are not using Clustering or not planning to do so you can ignore this Blog Post, as it would be supported to have 1 MEM config for all Servers. This blog will not take care on any Exchange Configuration and only handle the SEG options and explain one Example how it can work. There are cases where you want to use the “Clustering” option but still doing a Multi-Datacenter Configuration, if this is the case , this blog is exactly for you.
please make sure you are following the official Documentation on Secure Email Gateway here:
What is SEG Clustering ?
SEG can be configured in high availability and disaster recovery environments with both clustering and non-clustering server configurations. The high availability and disaster recovery setups are independent of the cluster configuration. When using SEG Clustering all SEG Servers of one MEM Config need to communicate to each other on the defined Ports (Default is 5701 & 41232) .
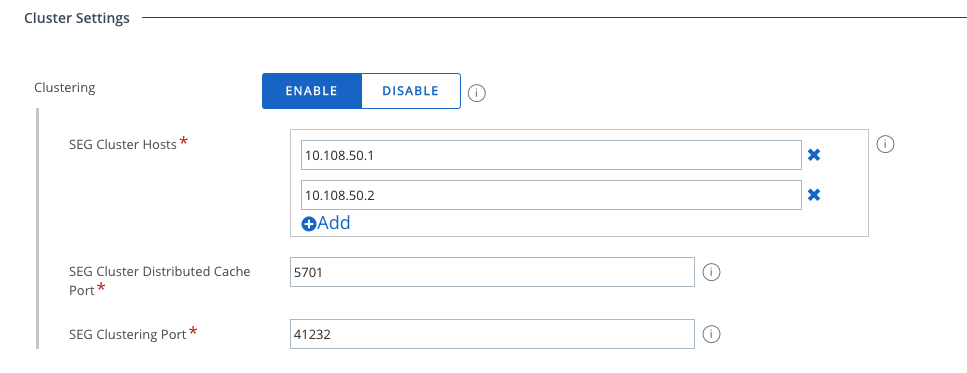
Once a device gets compliant or un-Compliant UEM send a message to the Public SEG URL in the Configuration with the updated details. If clustering would not be enabled , only one of the SEGs get the message. With Clustering the servers share this message with each other via a Distributed Cache. With out Clustering the Servers that did not reach the message instantly would use the Delta Sync that is by Default set to 10 Minutes in the Console and then get the updates.
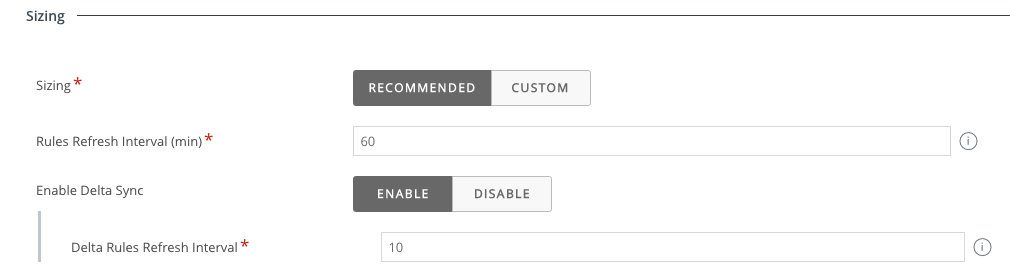
When clustering is enabled, policy updates are distributed to all SEGs in the cluster. The SEGs communicate with each other through the SEG clustering port.
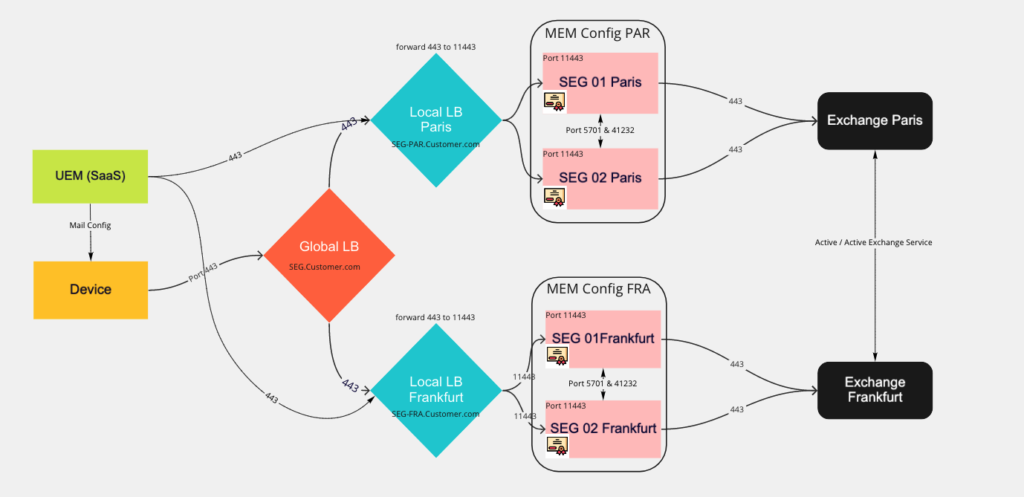
Multi Datacenter
If Clustering is used it is only supported to have one Mobile Email Management (MEM) Config per Datacenter. So we need to create 2 MEM Configs with 2 different URLs. This URLs can be different from the Device URLs, I decided to go with the Following:
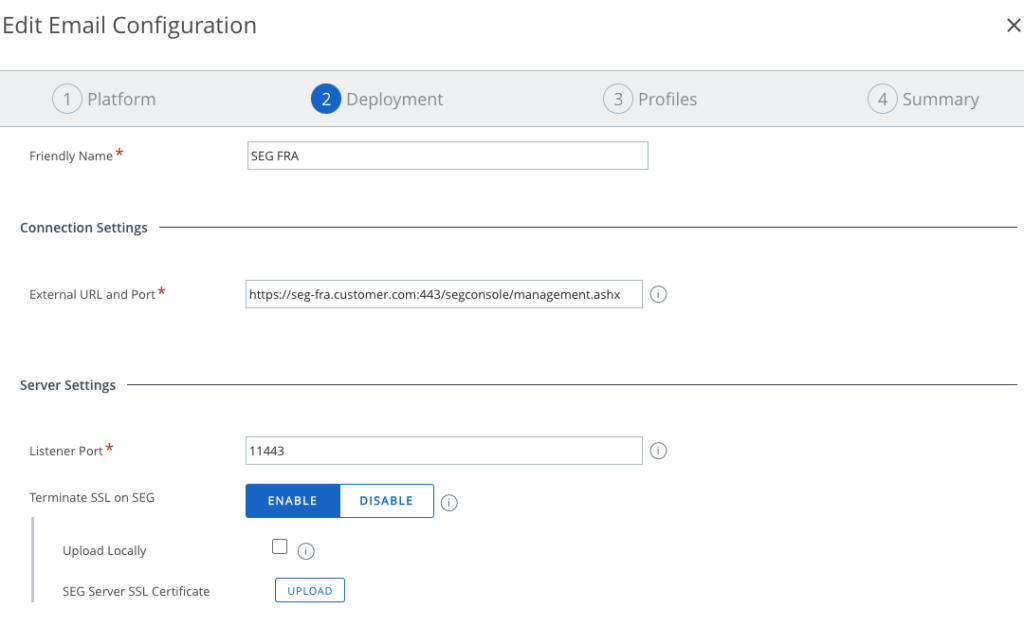
MEM Config Frankfurt uses URL SEG-FRA.Customer.com
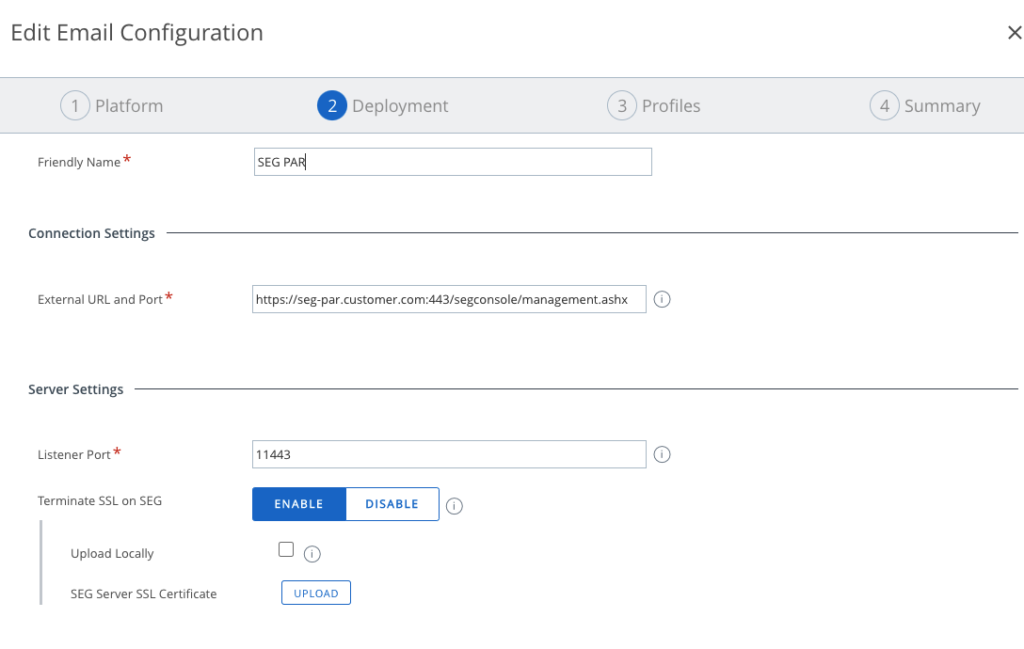
MEM Config Paris uses URL SEG-PAR.Customer.com
URL for the Devices: SEG.customer.com
So All 3 URLs need to be reachable from UEM/ Devices. UEM will use the URL in the MEM Config for the Device Policy Updates and Devices can use the Global URL. So once one Datacenter is down the global Loadbalancer just shifts the Traffic to the available Datacenter and Users will have access to the Mails without issues.
As it is common and always recommended on staying on the Port 443 the End User Email Traffic we used the Service Port 11443 locally on the UAG (where SEG is hosted) and shifted the 443 incoming traffic at the Local datacenter Loadbalancer from 443 to the 11443. This was done to remove the SNI Rule dependency from UAG to the Loadbalancer. As the UAG need to handle for Frankfurt for example SEG.customer.com & SEG-FRA.Customer.com which comes from Internet with port 443.
this is the Sample Config for the Frankfurt Datacenter:
For the other Datacenter (Paris) the Following config is used:
Note: Please also make sure the communication to Exchange is as short as possible, to directly use the Datacenter exchange and avoiding Cross Datacenter traffic if possible. To have a real active – active this is required even when one side just can break everything still works.
Loadbalancer & SSL Certificate
The SSL Certificate always needs to be trusted for the Device and it should also be trusted for UEM. So it is recommended to work with a Wildcard or with SAN names. I used Subject Alternative Names, to the Certificate has the subject “SEG.customer.com” for the Device Traffic and the SAN Attributes on “SEG-FRA.customer.com” & “SEG-PAR.customer.com” for the UEM Traffic.
I decided to not touch any SSL traffic , so the SSL Cert is on the UAG / SEG Service only. The Local Datacenter Loadbalancer is changing the incoming Port 443 to 11443 to not have to deal with SNI Rules on the UAG as it requires 2 URLs and by default only the MEM-Config URL is added here. The Loadbalancing rules should be used from the Recommended Architecture Guide of Omnissa Docs.
Overall Architecture
While this is a really complex Scenario the Architecture Diagram itself is looking quite simple.
While I added UEM in SaaS and the Device you clearly see the communication ways are different from Devices & UEM for the Inbound traffic. for Simplicity reasons the SEG to UEM API Communication is not shown here, but required as usual.
vExpert, blogger and VMware & Omnissa champion. Worked 10 years as a Architect for a partner before joining VMware in 2017. Moved to Omnissa in 2024.